Q.
|
What are the two CICS Signon transactions?
|
A.
|
CESN and CSSN.
|
Q.
|
What is the difference between CESN and CSSN?
|
A.
|
CESN is the sign-on transaction with the External Security Manager such as RACF. ESM user id and the associated password must be provided for CESN transaction. On the other hand, CSSN is the sign on the transaction without ESM. The OPNAME and PASSWORD defined in the SNT must be provided for this transaction.
|
Q.
|
What is the latest version of CICS?
|
A.
|
CICS TS Version 5.5
|
Q.
|
What are the two types of direct access files supported by CICS?
|
A.
|
VSAM and BDAM.
|
Q.
|
What are the two types of TD0s
|
A.
|
Intrapartition TDO and Extrapartition TDQ.
|
Q.
|
What is the difference between an Intrapartition TDQ and Extrapartition TDO?
|
A.
|
Intrapartition TDO is read or wrote by the program(s) in the same CICS system while Extrapartition TDQ is used by the applications outside the CICS system also.
|
Q.
|
What are the two types of interfaces provided by CICS to application programs?
|
A.
|
Command level and Macro level.
|
Q.
|
What is the function of the CICS translator?
|
A.
|
The CICS translator converts the EXEC CICS commands into call statements for a specific programming language. There are CICS translators for Assembler, PUI and COBOL.
|
Q.
|
What does 'pseudo conversational' mean?
|
A.
|
The programming methodology in which the task will not wait for the terminal user's response, but frees the resources after sending the message is called a pseudo-conversational technique. Terminating the task every time the application needs a response from the user and then starting the next transaction when the user presses any attention key is pseudo conversational processing.
|
Q.
|
Mainframe Forum: A comprehensive repository for programming tutorials and technology news. Got a minute? Click upon those blue words to start learning in Cobol, DB2, CICS, JCL, CA7, APIs, DevOps, Agile, JAVA, SORT, Excel macro, python, and mainframe tools.
Showing posts with label Tutorial. Show all posts
Showing posts with label Tutorial. Show all posts
Sunday, 21 April 2019
IBM-CICS Top 100 Question & Answers 2023 | IBM-CICS Interview Questions & Answers For Experienced & Fresher.
When to use which VSAM data set (i.e. EDS, KSDS, RRDS, LDS, ESDS) ?
 |
| Not sure when to use which data set. |
Being a programmer I have faced situations where you are not sure which VSAM data set is suitable for business applications.
In fact, as per my experience, there is the various factor that a programmer/designer should consider before finalizing data set which should be used for storing data.
In this tutorial, I have tried to compile key points that might help you in taking a decision.
Use KSDS if:
- The data access is sequential, skip sequential, or direct access by a key field
- You would prefer easy programming for direct data processing
- There will be many record insertions, deletions, and logical record length varies
- You may optionally access records by an alternate index
- Complex recovery (due to index and data components) is not a problem
- You want to use data compression.
Use RRDS if:
- The record processing is sequential, skip sequential, or direct processing.
- Easy programming for direct processing is not a requirement.
- The argument for accessing data in direct mode is a relative record number, not the contents of a data field (key). RRDS is suitable for the type of logical records identified by a continuous and dense pattern of numbers (such as 1,2,3,4...).
- All records are fixed length.
- There are a small number of record insertions and deletions, and all the space for insertions must be pre-allocated in advance.
- Performance is an issue. RRDS performance is better than KSDS but worse than QSAM or BSAM.
Use ESDS if:
- You are adding logical records only at the end of the data set and reading them sequentially (in the application control)
- The logical record is variable length
- You seldom need direct record processing by key (using AIX)
- You are using a batch processing application.
Use LDS if:
- You want to exploit DIV
- Your application manages logical records
- Performance is an issue.

Labels:
Alternate Index,
Catalog,
Cluster,
Commands,
Components,
ESDS,
File Status,
KSDS,
LDS,
Overview,
RRDS,
Tutorial,
Virtual Storage Access Method,
VSAM,
VSAM File,
VSAM Open Return Code,
Vsam Tutorial
A Summary Of The Characteristics Of VSAM Data Set Types | Comparing VSAM Data Set Organizations.
 |
| Characteristics Of VSAM Data Set Types |
I hope you have gone through my previous tutorial regarding VSAM terminology and concept. As you are already aware that there are 4 types of VSAM cluster/data sets i.e. KSDS, ESDS, LDS, RRDS.
In this tutorial, I have tried to compare the characteristics of the VSAM data set (i.e. ESDS, KSDS, RRDS, VRRDS).
This comparison of the VSAM data set organization would help you to understand the difference of each cluster.
The table provides a summary of the characteristics of VSAM data set types.
ESDS | KSDS | Fixed-length RRDS | Variable-length RRDS | Linear data sets |
Records are in the same order as they are entered | Records are in collating sequence by key field after load | Records are in relative record number order | Records are in relative record number order | No processing at a record level |
Records can be fixed or variable length | Records can be fixed or variable length | Records are fixed length | Records are variable length | No processing at a record level |
Direct access by RBA | Direct access by key or by RBA | Direct access by relative record number | Direct access by relative record number | Access with Data-In-Virtual (DIV) optionally |
Consist of a data component only | Consist of data and index components | Consist of a data component only | Consist of data and index components | Consist of a data component only |
Alternate index allowed | Alternate indexes allowed | No alternate index allowed | No alternate index allowed | No alternate index allowed |
A record’s RBA cannot change | A record’s RBA can change | A record’s relative record number cannot change | A record’s relative record number cannot change | No processing at a record level |
Space at the end of the data set is used for adding records | Free space is used for inserting and lengthening records | Empty slots in the data set are used for adding records | Free space is used for inserting and lengthening records | No processing at a record level |
A record cannot be deleted, but you can reuse its space for a record of the same length | Space that is given up by a deleted or shortened record becomes free space | A slot that is given up by a deleted record can be reused | Space that is given up by a deleted or shortened record becomes free space | No processing at a record level |
Spanned records allowed | Spanned records allowed | No spanned records | No spanned records | No spanned records |
Extended format allowed | Extended format or compression allowed | Extended format allowed | Extended format allowed | Extended format allowed |

Labels:
Alternate Index,
Catalog,
Cluster,
Commands,
Components,
ESDS,
File Status,
KSDS,
LDS,
Overview,
RRDS,
Tutorial,
Virtual Storage Access Method,
VSAM,
VSAM File,
VSAM Open Return Code,
Vsam Tutorial
Friday, 12 April 2019
How to define VSAM CLUSTER / VSAM File? | Command to define VSAM Database.
To create a VSAM dataset/ VSAM file you need to use AMS (i.e. Access Method Service).
Most of the ASM commands are used very often and almost every mainframe application programmer remember these commands.
As you can see, these include commands for defining all three types of VSAM datasets / Clusters, for defining and building alternate indexes for key-sequenced data sets, and for listing catalog information.
However, there are basically two ways of defining a cluster i.e. maybe you can use JCL or ISPF panel.
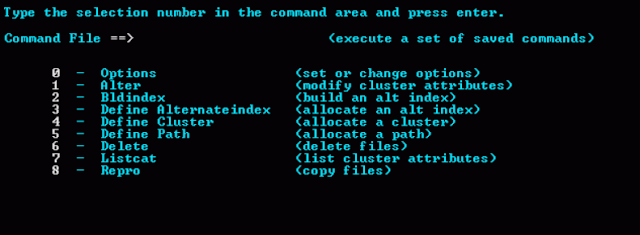 |
| ISPF panel to define VSAM cluster. |
The DEFINE CLUSTER command is used to define a KSDS, ESDS, or RRDS.
Please note that parameters at the CLUSTER level apply to the entire cluster and parameters at the DATA or INDEX level apply only to the data or index component.

Labels:
Alternate Index,
Catalog,
Cluster,
Commands,
Components,
ESDS,
File Status,
KSDS,
LDS,
Overview,
RRDS,
Tutorial,
Virtual Storage Access Method,
VSAM,
VSAM File,
VSAM Open Return Code,
Vsam Tutorial
Wednesday, 10 April 2019
VSAM - Virtual Storage Access Method Concepts.
Virtual Storage Access Method which is popularly known as VSAM. VSAM is one of several access methods in z/OS. It applies only to data stored on direct access storage devices (DASDs).
VSAM access method is used for indexed files on an IBM mainframe. It was introduced by IBM in the 1970s. This access method makes it easier for an application to run an I/O operation (moving data between an I/O device and memory)
VSAM access method is used for indexed files on an IBM mainframe. It was introduced by IBM in the 1970s. This access method makes it easier for an application to run an I/O operation (moving data between an I/O device and memory)
It is a high-performance access method used to organize data in the form of files in Mainframes.
The word virtual means only that VSAM was introduced at approximately the same time as the initial IBM virtual storage operating systems OS/VS1 and OS/VS2. Since then VSAM has been continually improved and enhanced.
The word virtual means only that VSAM was introduced at approximately the same time as the initial IBM virtual storage operating systems OS/VS1 and OS/VS2. Since then VSAM has been continually improved and enhanced.
It provides a catalog facility that can be used for both VSAM and non-VSAM files. And it provides a multi-function utility program called Access Method Services (AMS) that lets you perform a variety of functions for VSAM as well as non-VSAM files.
 |
| IBM Mainframe Architecture. |
Type of Data set:
VSAM data sets are broadly categorized into 4 categories.
- ESDS: Entry-sequenced data set (ESDS), the records are stored one after the other in consecutive disk locations. On other platforms, this is called a sequential file.To retrieve records from a sequential file, you must read them sequentially by disk location. This type of record retrieval is referred to as sequential access.
- KSDS: A key-sequenced data set (KSDS) consists of two parts: an index component and a data component. Within the index component, each entry contains a key field value that points either to a lower-level index or to a record in the data component of the file. On other platforms, this type of data set is called an indexed file.
- RRDS: A relative-record data set (RRDS) consists of record areas that can contain one record. Each of these areas is identified by a relative record number that indicates its relative position in the file. On other platforms, this type of data set is called a relative file.
- LDS: A Linear data set (LDS) contains data that has no record boundaries. Linear data sets contain none of the control information that other VSAM data sets do. Linear data sets must be cataloged in an integrated catalog facility catalog.
- The retrieval of records is faster because of an efficiently organized index. The index is small because of key compression algorithm used to store and retrieve records
- Embedded free space makes the insertion of records easy and therefore requires less reorganization
- The deletion of records means that they are physically deleted thus allowing the reclaiming of free space within data sets
- Records can be accessed randomly by key or address and can also be accessed sequentially at the same time
- VSAM data sets can be shared across partitions, regions, address space and systems. The type and level of sharing can be controlled thru AMS and JCL
- VSAM provides data security thru passwords protection of data sets at various levels like reading an update.
- VSAM provides the ability to physically distribute datasets over various volumes based on key ranges.
- VSAM data sets are device independent
Drawbacks:
- Free spaces, hence more disk space
- The integrity of VSAM data sets in cross systems and cross regions sharing must be controlled by the User.
 Have a look of Top 20 Interview Questions for VSAM (Virtual Storage Access Method)..
Have a look of Top 20 Interview Questions for VSAM (Virtual Storage Access Method)..

Labels:
Alternate Index,
Catalog,
Cluster,
Commands,
Components,
ESDS,
File Status,
KSDS,
LDS,
Overview,
RRDS,
Tutorial,
Virtual Storage Access Method,
VSAM,
VSAM File,
VSAM Open Return Code,
Vsam Tutorial
How to schedule a job for a specific system?
 |
| How to schedule a job for a specific system? |
In a multiprocessor network, each system operates under the control of its own copy of OS/390 or ZOS.
However, the JES components of each processor’s operating system are connected in various ways to the JES components of the other processors, and a common spool is used to service all the processors in the network.
 |
| IBM Mainframe Architecture |
As a result, JES2 and JES3 can control how jobs are processed by the systems within the multiprocessor network.
- The term system affinity can be used to describe the relationship between a job and the system on which it executes.
- Under JES2, you use the SYSAFF parameter of the /*JOBPARM statement to specify system affinity.
- Under JES3, you use the SYSTEM parameter of the //*MAIN statement.
The global processor is the processor that’s in charge of the entire network. A local processor is one that’s controlled by the global processor.
The syntax for the SYSAFF parameter of the JES2 /*JOBPARM statement
SYSAFF= {*} {(system-name,…)} {ANY}
Explanation
* | The job will run on the system that reads it (the default). |
system-name | A one- to four-character system-id defined in the multiprocessor network that identifies which processor will run the job. If more than one system-name is specified, the job can run on any one of the processors listed. |
ANY | The job can run on any available processor. |
The syntax for the SYSTEM parameter of the JES3 //*MAIN statement
SYSTEM= {[/](main-name,…)} {JGLOBAL} {JLOCAL} {ANY}
main-name | A system-id defined in the multiprocessor network that identifies which processor will be used to run the job. If more than one main-name is specified, the job can run on any one of the processors listed. |
/ | The job can run on any processor except the one(s) listed. |
JGLOBAL | The job must run on the global processor. |
JLOCAL | The job can run on any local processor. |
ANY | The job can run on any available processor. |
Specifying system affinity
Under JES2
/*JOBPARM SYSAFF=MVSA
/*JOBPARM SYSAFF=(MVSA,MVSB)
/*JOBPARM SYSAFF=ANY
Under JES3
//*MAIN SYSTEM=(MVSA,MVSC,MVSD)
//*MAIN SYSTEM=JLOCAL
//*MAIN SYSTEM=/MVSB
 |
| Mainframe-Forum |

Tuesday, 9 April 2019
How to create and use cataloged procedures.
 |
| JCL Catalog Procedure's |
By using procedures/JCL catalog procedure, the amount of JCL coding you have to do is reduced, resulting in fewer coding errors and greater productivity.
Definition of cataloged procedure.
A cataloged procedure is a series of JCL statements that are stored in a partitioned data set and may be invoked by any job on the system.
Typical types of cataloged procedures
- IBM-supplied procedures that compile, link, and run programs
- JCL steps that back up, delete and define VSAM files
- Programs that are required by many jobs
- Large jobs where it makes sense to separate the steps into manageable procedures.
Cataloged procedures are stored in partitioned data sets and can be invoked by any job on the system. When you invoke a cataloged procedure, the system looks for it in the system procedure library, SYS1.PROCLIB, unless you specify otherwise.
The syntax for invoking a JCL procedure
EXEC [PROC=]procedure-name
Explanation
| procedure-name | Identifies the procedure to be called and executed. For cataloged procedures, it’s the member name of the procedure. For in-stream procedures, it’s the name on the PROC statement that begins the procedure. |
Example:
A job that invokes a cataloged procedure
//STEP1 EXEC TMP3000
//
The cataloged JCL procedure named TMP3000 that is invoked
//TMP3010 EXEC PGM=EMP33010
//SYSOUT DD SYSOUT=*
//INVMAST DD DSNAME=RCA2.INVE.MASTER.FILE,DISP=SHR
//INVSEL DD DSNAME=&&INVSEL,DISP=(NEW,PASS),
// UNIT=SYSDA,SPACE=(CYL,(20,10))
//SELCTL DD DUMMY
//INV3020 EXEC PGM=EMP3020
//SYSOUT DD SYSOUT=*
//INVMAST DD DSNAME=&&INVSEL,DISP=(OLD,DELETE)
//INVSLST DD SYSOUT=*

Saturday, 6 April 2019
Top 20 Interview Questions for VSAM (Virtual Storage Access Method)
 |
| Top 20 Interview Questions for VSAM. |
Q. | What are the types of VSAM DataSets? |
| A. | Entry sequenced DataSets (ESDS), Key sequenced DataSets (KSDS) and relative record (RRDS), LDS (linear Data Set). |
| Q. | Why do VSAM take more disk space than other utilities? |
| A. | VSAM increases the disk space requirements of systems. This is because VSAM offers certain capabilities like partial self-reorganization to make things more efficient in data sets that can be modified. |
| Q. | What are the distinctive features of a KSDS, Key sequenced DataSet? |
| A. | The index and the distributed free space. CI and CA split upon updates. Record length may be changed during the update. The records are accessed by a particular Key. |
| Q. | How are records stored in an ESDS, entry sequenced DataSet? |
| A. | They are stored without respect to the contents of the records and in the order in which they are included in the file. |
| Q. | What's an LDS (Linear Data Set) and what's it used for? |
| A. | LDS is a VSAM DataSet in name only. It has unstructured 4k (4096 bytes) fixed size CIs which do not contain control fields. There is no free space, and no access from Cobol. LDS is essentially a table of data maintained on disk. The 'table entries' must be created via a user program and can only be logically accessed via a user program. When passed, the entire LDS must be mapped into storage, then data is accessed via base and displacement type processing. |
| Q. | In ESDS, do we have the facility of accessing the records randomly? |
| A. | YES, Random access to records is possible. Records, however, cannot be deleted. We can do it by referring to the RBA (relative byte address). |
| Q. | Why is space is kept in the data component of the KSDS DataSet? |
| A. | Free space specified during the allocation of the KSDS is left at regular intervals during the initial load of the data set. This space helps keep the data component in physical sequence in spite of random insertions. |
| Q. | What is the difference b/w the ESDS and KSDS? |
| A. | ESDS doesn’t have embedded free space. The KEYS parameter has no meaning in the context of ESDS ESDS has no index component. An additional parameter, NONINDEXED is used to tell AMS that an ESDS is being allocated. |
| Q. | How is LDS different from ESDS? |
| A. | An LDS is a data set, very similar to an ESDS without the control information.It has no records and used for fast random access. It takes advantages of the computer’s very fast paging hardware for retrieval and storage and the bytes are implicitly divided into 4K blocks or pages, and the paging hardware reads and writes blocks from disk. There is no free space, unused space, control field in LDS. |
| Q. | What is a CI, Control Interval? |
| A. | A Control Interval is the unit of information that VSAM transfers between virtual and auxiliary storage. |
| Q. | What is Control Interval Split? |
| A. | A new record stored in the same CI, only if there is enough space. If not VSAM locates the free CI within the same CA, moves approximately half of the records to next CI and stores the new record at the correct position. This is called Control Interval Split. Whenever CI split occurs the sequence set is updated. |
| Q. | What is a CA, control area? |
| A. | A group of Control Intervals makes up a control area. |
| Q. | If the records are larger than the CI size, for ex. if a record extends CI boundary and extends unto 3 CI, and there is still some space left in last i.e. third CI, will that be used by other CI DataSets? |
| A. | NO. Some records are larger than the CI size, the records extend across CI boundaries (only for ESDS and KSDS). A spanned record begins on a CI boundary and it occupies two or more CIs in a CA. The unused space in the last CI can only be used to extend the record, it cannot contain any other record i.e. a new record has to be added in a new CI. |
| Q. | What is a sequence set? |
| A. | This is the part of the index that points to the CA and CI of the record being accessed. |
| Q. | What is a cluster? |
| A. | A cluster is the combination of the index, sequence set and data portions of the DataSet. The operating system gives program access to the cluster, i.e. to all parts of the DataSet simultaneously. |
| Q. | What is the index set? |
| A. | This is the other part of the index. It has multiple levels with pointers that ultimately reach to the sequence set. |
| Q. | What is a Catalog? |
| A. | The catalogue contains the names of all DataSets, VSAM and non-VSAM. It is used to access these datasets. |
| Q. | What is an alternate index? |
| A. | An AIX is a file that allows access to a VSAM DataSet by a Key other than the primary one. The alternate Key-pointer pair records are stored in an index cluster. This index cluster is known as the alternate index. The alternate Key-pointer pair records are loaded into the alternate index cluster by the command BLDINDEX.AIX can be built over a KSDS and ESDS, but not over an RRDS. |
| Q. | What could be the maximum number of the AIXs per base cluster? |
| A. | There can be a maximum of 253 AIXs per base cluster. It is not advisable to have more than 5 AIXs per base cluster because of additional overhead during updates and retrievals. |
| Q. | Can AIX be defined over an ESDS, which does not have any Key? |
| A. | Although an ESDS does not have a primary Key, an AIX can be defined over an ESDS. In the case of an ESDS it is the relative byte address of the corresponding record in the base cluster that is stored. |
| Q. | Can we access records in VSAM only by a single Key, i.e. primary Key? |
| A. | It is also possible to access the records in a sequence other than that of the primary Key. Such Keys are called alternate Keys and they can be non-unique. For Example, in a pay-roll system where employee number is the unique primary Key and the employee name as alternate Key. |
| Q. | What is the 'verify' command in the VSAM files ? |
| A. | This command is used to close those files that are kept open after the abnormal termination of the file. It also brings the index component in sync with the data components and updates the catalog. |
| Q. | What is a path? |
| A. | A path is a file that allows you to access a file by alternate index - the path provides an association between the AIX and the base cluster. |
| Q. | What is the upgrade set? |
| A. | The upgrade set is the list of all AIXs that VSAM must maintain for a specific base cluster, so that when data in the base cluster is updated, the AIX files are also updated. |
| Q. | What is free space? |
| A. | Free space is reserved within the data component of a KSDS to accommodate inserting new records. |
| Q. | What is IDCAMS? and what is the purpose of it?. |
| A. | IDCAMS, also known as Access Method Services, is used to perform the following tasks: * Create a VSAM data set, VSAM alternate index, or catalog. * List a catalog entry for a data set, DataSet/catalog contents. * Copy a DataSet or catalog . * Convert non-VSAM to VSAM data set . * Load a VSAM DataSet from VSAM records * Rename VSAM data sets. |
| Q. | What is a VSAM split? |
| A. | If there isn't enough space in the Control Interval VSAM performs a Control Interval split by moving some records to the free Control Intervals. If there isn't a free Control Interval VSAM performs a control area split by allocating a new control area and moving half of the Control Intervals to it. |
| Q. | What is the base cluster? |
| A. | The base cluster consists of the data component and the index component for the primary index of a KSDS. |
| Q. | What will happen if there is no secondary allocation made for DataSets? |
| A. | VSAM will inform COBOL program of the problem and terminate the processing of the program. |
| Q. | Why CI and CA splits are not possible in ESDS and RRDS? |
| A. | In ESDS the new record is added at the end of last record. And no imbedded free space is allocated at the time of DataSet definition. In the case of RRDS the slots for the records are preallocated and so the CI and CA split is not possible. |
| Q. | Do primary Key values have to be unique? Do alternate Key values have to be unique? |
| A. | Primary Key values must be unique; alternate Key values need not be. |
| Q. | In the COBOL SELECT statement what is the ORGANIZATION for a KSDS? |
| A. | The ORGANIZATION is INDEXED. |
| Q. | In the COBOL SELECT statement for a KSDS what are the three possibilities for ACCESS? |
| A. | ACCESS can be SEQUENTIAL, RANDOM or DYNAMIC. |
| Q. | What is the COBOL RECORD KEY clause? |
| A. | The RECORD KEY in the SELECT clause identifies the files primary Key as it will be known to the program. |
| Q. | What is the purpose of the FILE STATUS clause in the SELECT statement? |
| A. | The FILE STATUS field identifies the field that VSAM uses to provide information about each I/O operation for the file. |
| Q. | If you wish to use the REWRITE command how must the VSAM file be opened? |
| A. | It must be opened I/O mode. |
| Q. | Explain the meaning and syntax for the START command? |
| A. | The START command is used to read other than the next VSAM record. A value must be moved into the RECORD KEY. The KEY clause is optional, but it can be used to specify relational (equal, less than, etc.) operator. |
| Q. | What is the meaning of dynamic processing? |
| A. | It means one program uses both sequential and random processing for a VSAM KSDS file. It's rarely used. |
| Q. | Name some common VSAM error conditions and codes? |
| A. | They are end of file (10), duplicate Key (22), record not found (23), Out of space condition is raised (28) ,VSAM logic error (90), open problem (92) and space problem (93). |
| Q. | What is the VSAM-code field? |
| A. | It is a COBOL II enhancement to VSAM batch processing expanding the FILE STATUS field. It is defined in WORKING - STORAGE as a six byte group item with three two byte elements, the normal return code, the function code and the feedback code. |
| Q. | What is a VSAM slot? |
| A. | A relative record DataSet (RRDS) consists of a specified number of areas called slots. Each slot is identified by a relative record number (RRN) which indicates its relative position in the file. |
| Q. | What is the utility program closely associated with VSAM? |
| A. | IDCAMS, the access method services utility. |
| Q. | There are at least seven IDCAMS commands; name and explain each of them? |
| A. | ALTER modifies information for a catalog, alternate index, cluster or path. BLDINDEX builds the alternate index, of course. DEFINE is used for ALTERNATEINDEX, CLUSTER or PATH. DELETE removes the catalog entry for a catalog, cluster, alternate index or path. LISTCAT lists information about the DataSet. PRINT prints the DataSet contents. REPRO copies records from one file to another. |
| Q. | What are the three levels of definition for the VSAM DEFINE? |
| A. | They are DEFINE CLUSTER, DATA and INDEX. |
| Q. | What is the significance of the SHAREOPTIONS parameter? |
| A. | It specifies how the file may be shared between jobs and between batch and CICS environments. |
| Q. | What is the meaning of the DEFINE MODEL parameter? |
| A. | It specifies whether the MODEL parameter allows you to model your cluster by modelling it after an existing cluster. |
| Q. | How do you fix the problem associated with VSAM out of space condition? |
| A. | 1. Define new VSAM DataSet allocated with more space. 2. Use IDCAMS to REPRO the old VSAM file to new VSAM DataSet. 3. Use IDCAMS to ALTER / rename the old VSAM DataSet or set IDCAMS to DELETE the old VSAM DataSet. 4. Use IDCAMS to ALTER / rename the new VSAM DataSet to the name of the original VSAM DataSet. |
| Q. | In how many ways can you load the data in a VSAM cluster? |
| A. | 1. Using the REPRO command. 2. Using COBOL program |
| Q. | What is the REPRO command? |
| A. | While a new cluster is created using IDCAMS, cluster will be empty. By using the REPRO command, we can load records into the cluster. REPRO is Used to : • Copy DataSets (VSAM or NON-VSAM), copy catalogs. • Convert sequential and index sequential DataSets to VSAM format • Convert VSAM and Index sequential DataSets to sequential format • Backup VSAM catalog • Read a backup copy of VSAM catalog |
| Q. | Is it slower if you access a record through ALTERNATIVE INDEX as compared to Primary INDEX? |
| A. | YES. Because the alternate Key would first locate the primary Key, which in turn locates the actual record. Needs twice the number of I/Os. |
| Q. | What is RECOVERY and SPEED parameters in DEFINE CLUSTER command? |
| A. | RECOVERY (default) and SPEED are mutually exclusive. Recovery pre-formats the control areas during the initial DataSet load, if the job fails, you can restart but you must have a recovery routine already written to restart the job. SPEED does not pre-format the CAs. It is recommended that you specify SPEED to speed up your initial data load. |
| Q. | What is a SHAREOPTIONS parameter (SHR) in Define Cluster command. |
| A. | It defines the cross-region and cross-system sharing capabilities of the DataSet. Syntax is SHR (CRvalue CSvalue) 1 means multiple read OR single write (read integrity) 2 means multiple read AND single write (Write integrity) 3 means Multiple read AND multiple write 4 is same as 3, which refreshes the buffer with every random access. Default is SHR (1 3). |
| Q. | What are the optional parameters to the input DataSet While loading the empty cluster with the data records? |
| A. | i) Skip and Count Syntax: SKIP(2) COUNT(4) In this case, the first two records are skipped and the next four records are printed. The default for SKIP is 0, and for COUNT will be printing records from beginning to end. ii) FromKey and ToKey PRINT - INDATASET (CUSTOMER.KSDS.CLUSTER) - FROMKEY (111111) - TOKEY (444444) Will print all records with Key value ranging from 111111 to 444444. iii) FROMADDRESS and TOADDRESS iv) FROMNUMBER and TONUMBER |
| Q. | What does GDG mean in VSAM? |
| A. | Generation Data Group |
| Q. | Is a delete operation possible in an ESDS? Is rewrite operation possible in ESDS ? |
| A. | No. Delete operation is not possible in VSAM ESDS. Yes, rewrite operation is possible in an ESDS |
| Q. | Can VSAM files be deleted with the DELETE option of the DISPOSITION parameter of JCL? |
| A. | No, you have to give a separate DELETE command in the VSAM cluster. |
| Q. | How many buffers are allocated to VSAM KSDS and ESDS? |
| A. | 2 data buffers by default for ESDS. For KSDS it allots 2 data buffers and 1 index buffers. Each buffer is about 4k. |
| Q. | What are the codes returned by the AMS (Access Method Services) command during the execution? |
| A. | Every AMS command issues a condition code. If multiple commands are being executed successively, there might be a requirement to execute or bypass certain commands on the success or failure of a previous command. 0 - The function was executed successfully 4 - A problem was encountered while executing the function, WARNING 8 - The requested function was executed, but major specifies were unavoidably bypassed, ERROR 12 - The requested command could not be performed because of a logical error, SEVERE 16 - A severe error occurred causing the remainder of the command stream to be bypassed., FATAL. |
 |
| Share VSAM Interview Questions. |

Labels:
Alternate Index,
Catalog,
Cluster,
Commands,
Components,
ESDS,
File Status,
Interview Questions,
KSDS,
LDS,
Overview,
RRDS,
Tutorial,
Virtual Storage Access Method,
VSAM,
VSAM File,
Vsam Tutorial
Subscribe to:
Posts (Atom)