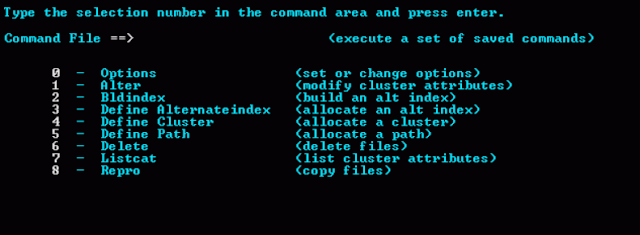
In this tutorial, I would try to focus on the latest trends in mainframe (The Big Iron) application development. The new methodology is more efficient, faster and cost effective as compare to old terminology.
The software industry is continuously evolving with the introduction of new methodologies such as DevOps and a set of new tools (i.e. IBM UrbanCode Deploy, RDZ, DevOps Azure) that improve process efficiency.
In the traditional software delivery pipeline, developers write code in an integrated development environment (IDE), such as Eclipse. The application is deployed to the test environment, then a pre-production or staging environment, and finally the production environment.
The DevOps delivery pipeline has all the same phases. But, it adds automation and continuous feedback loops, so more things happen automatically, and the deliverable artifact can improve with each develop-build-deploy cycle.
You will be surprised to know that DevOps-style continuous delivery is also supported by Mainframe Systems (for example CICS Transaction Server). Let me give a brief explanation of the term DevOps.
What is DevOps or DevOps Meaning?
DevOps = Software Development and Information Technology Development.
DevOps is a software development methodology that stresses intercommunication between software developers and other personnel such as testers, designers, quality assurance, and operations. Since the term was initially coined to describe the collaboration between software developers and operations personnel, both roles were concatenated to form the word DevOps.
DevOps is a direct descendant of the more established Agile software methodology. DevOps is fairly new. The term was first used at an Agile conference in 2008. The name has stuck and has created a full-blown methodology. DevOps has created new ideas about how organizations create and maintain software. DevOps has also created an ecosystem full of tools and other solutions that claim to be DevOps.
 |
| DevOps Methodology Overview. |
The goal of
DevOps is to leverage collaboration throughout the entire software development life cycle. Another cornerstone of
DevOps is blurring some of the traditional responsibilities of the personnel involved in software development.
DevOps specifies the certain responsibilities and tasks that traditionally would be held by a single group – that is developers write test code and operations personnel set up servers – are now shared.
This collaboration will result in faster development times, better quality code, increased efficiency, quality assurance, user acceptance, and production support. Of course, since
DevOps is so new, there are still many questions on how to measure the benefits of
DevOps.
There are many underlying reasons that can be attributed to the emergence of DevOps. A major factor is the evolution of software. Traditionally, the software was developed to complete a business or technical task and programmers wrote them.
This software program needs to run on a computer. Network operators would provide and maintain the computer on which developers program their software. Generally, there are two different groups here – developers and operations personnel. Each group has a mutually exclusive, predefined role.
Recently, the software has evolved to perform tasks such as emulation and virtualization. Developers can now deploy programs on virtual machines, often without the assistance of operations provisioning a physical server.
Clearly, there needs to be collaboration and coordination between developers and operations. This collaboration is called DevOps.
Many IT experts predict that as new technologies emerge that require more interfaces to more channels, the DevOps approach will gain popularity for the speed with which it can generate releases and updates.
Is DevOps is just a collaboration?
Of course, DevOps is more than this. DevOps collaboration is not limited to developers and operations. Adopters of DevOps identify different groups within their software infrastructure and the tasks they perform.
Each group and task is analyzed to identify any areas of interdependence that can be added as collaborative efforts. DevOps intends to blur the traditional lines within the software development infrastructure.
It is hoped that – since traditional tasks are now a shared collaborative effort – each group will feel more invested in tasks that they did not traditionally perform.
To name a couple, developers will write better code as they are now partners in the quality assurance process and operations staff may spend more time on security patches as they discover network impact on the software development life cycle.
DevOps Benefits:
In a DevOps, the business owner, the developers, and the operations team work collaboratively. The plan-develop-build-deploy-feedback process is continuous. The possible, human actions are minimized in favor of autonomous tools, including software builds that start on their own when eligible code updates become available.
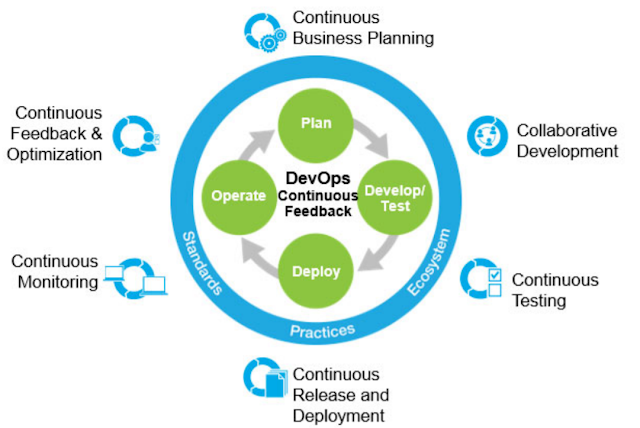 |
| DevOps Overview |